Build your digital asset advantage
The Taurus platform connects everything
you need to custody and manage any digital asset
you need to custody and manage any digital asset




















Unified platform
Everything you need to custody and manage any digital asset.
Cryptocurrencies
Securely custody and manage the widest range of cryptocurrencies including staking and DeFi
Find out more >Tokenized assets
Digitize and tokenize any type of assets, securities on any standard, including NFTs
Find out more >Digital currencies
Digitally issue, book and transfer any stable coin or digital currencies and optimize your settlement process
Find out more >
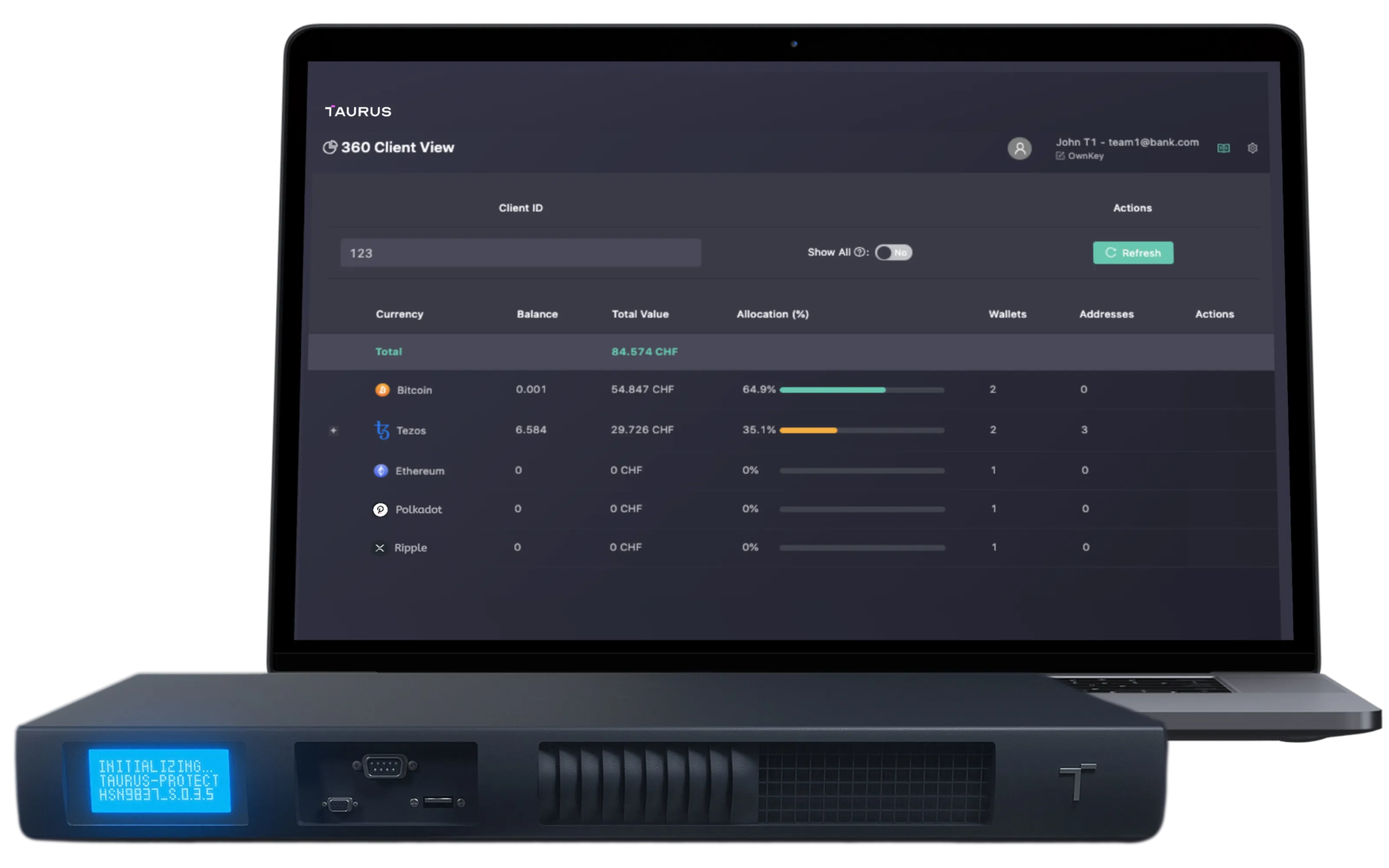
Hot, warm and cold custody platform
Custody and process any digital asset: crypto-assets, tokenized securities, digital currencies.

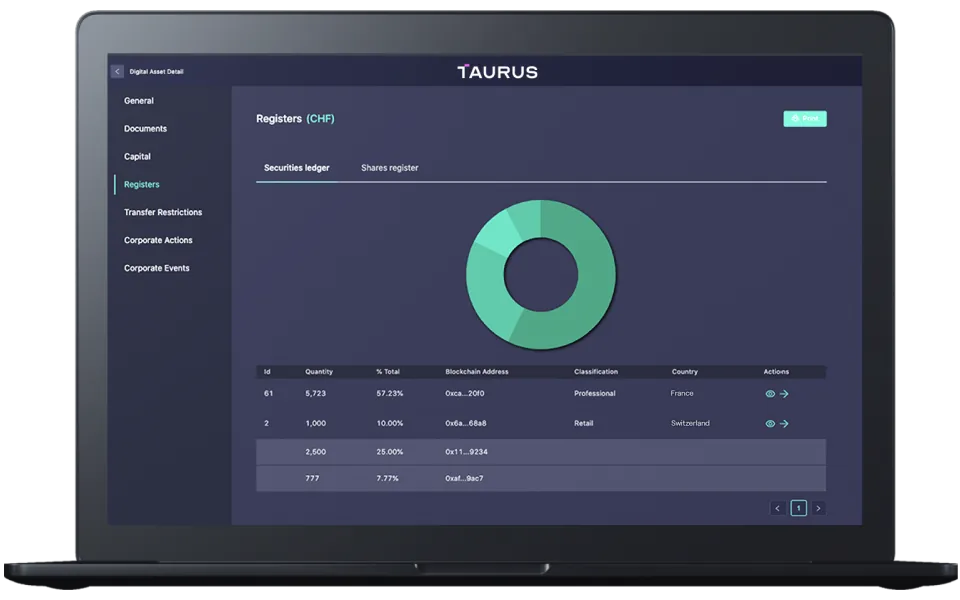
Digital issuance and tokenization platform
Digitally issue, book, and manage tokenized assets across their full lifecycle without limit. On any standard.

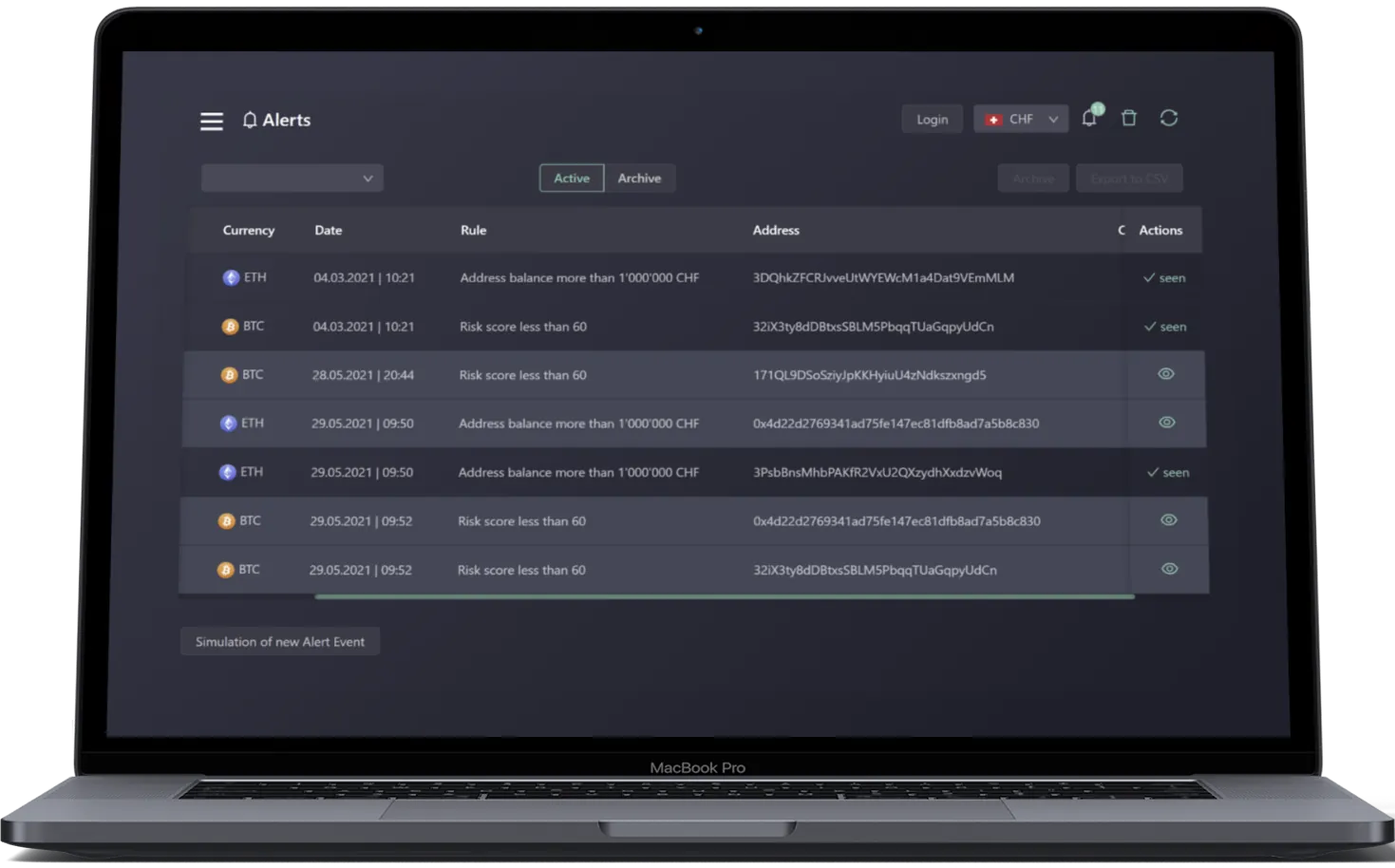
SaaS blockchain connectivity and indexing
Unified API to interact with 10+ blockchain protocols. Transfer assets, monitor wallets and manage counterparty risk, all in real-time.

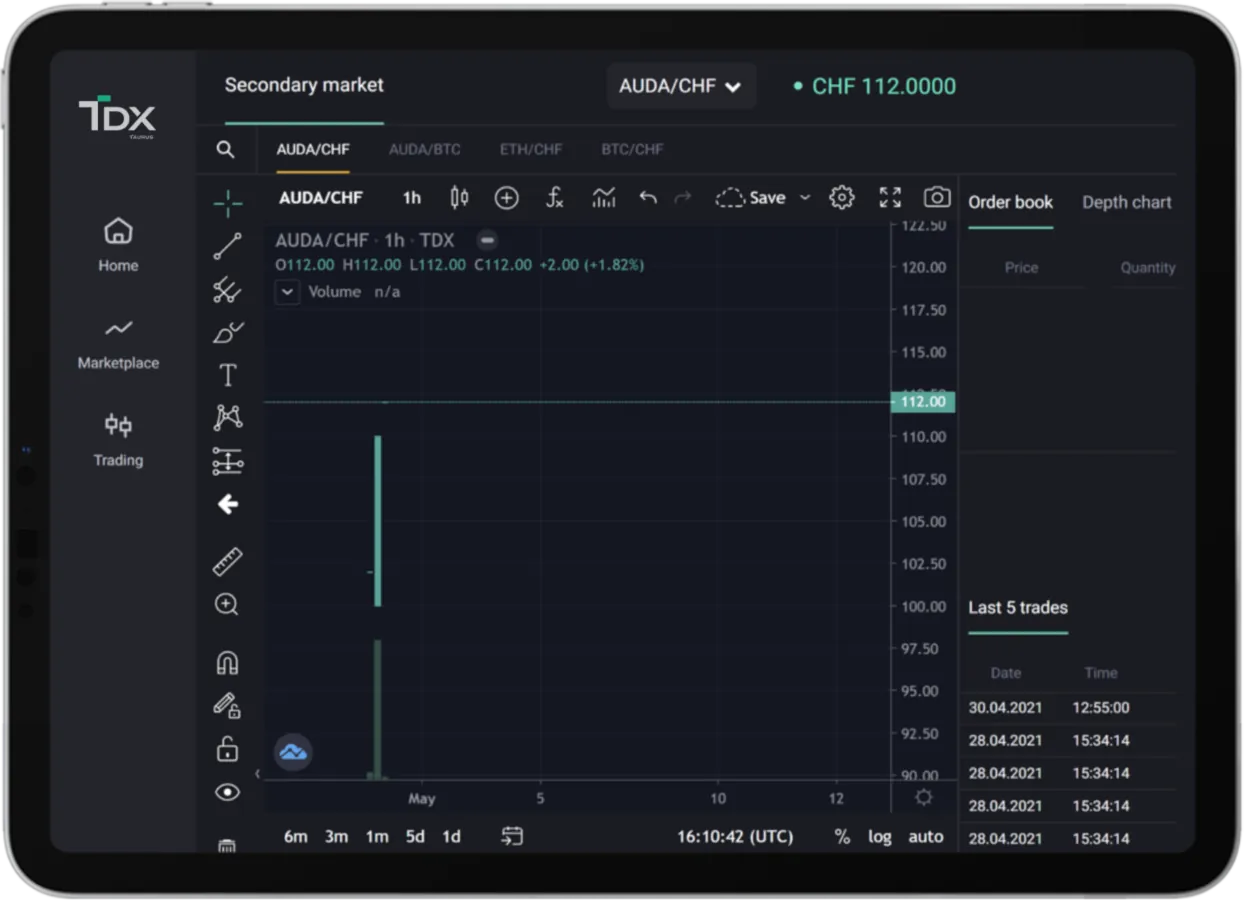
Regulated digital asset marketplace
Trade and manage any digital asset and tokenized securities. Unlock liquidity for banks, shareholders and even artists.
Industry-leadingtechnology.Fast and flexibledeployment.
- Certified, award winning technology
- Public, private blockchains, tokenized assets
- On premise, SaaS, hybrid deployment
- As little as 10 days for go-live
#1 platform for banks. See why
More than half of banks offering digital assets run on Taurus infrastructure in Switzerland.
Entrusted and in production with the full spectrum of financial institutions
We are delighted to have found a very innovative partner in Taurus. With Taurus' products, we can offer our customers an expanded range of investment opportunities in the field of digital assets.
Taurus is leading the field in cryptography and blockchain technology. By joining forces, we can help banks to bridge the gap between traditional investments and digital assets.
As the digital asset space is expected to encompass trillions of dollars of assets, it’s bound to be seen as one of the priorities for investors and corporations alike. As such, custodians must start adapting to support their clients, This is why we are excited to partner with Taurus, a leading digital asset infrastructure provider with a proven track record and extensive expertise in the crypto and tokenization space.



Banking-Grade Custody
22.06.2023
Critical aspects involved in establishing a banking-grade custody solution for digital assets.
read more >
Tokenization: practitioner point of view
22.03.2023
All you need to tokenize successfully any asset
read more >
Scalability solutions, Ethereum L2s - part 1
31.01.2022
All you need to know about Ethereum L2 protocols and scalability solutions
read more >
Introduction to NFTs
14.01.2022
Discover the NFTs market landscape, the main collections and what we should expect next
read more >
Introduction to DeFi
02.07.2021
Find out what is DeFi, why it matters, and what are the challenges ahead?
read more >